關於 Byte-Tron Solutions
領先的網絡安全專家,致力於保護企業免受數碼威脅。
您值得信賴的安全合作夥伴
在 Byte-Tron Solutions,我們深知網絡安全不僅關乎技術,更關乎保護您的業務、客戶和未來。憑藉在網絡安全行業超過十年的經驗,我們已協助數百家企業建立強大的防禦體系,以應對不斷變化的數碼威脅。
100+
受保護系統
25+
服務國家
25+
專業認證
99.9%
客戶保留率

Expertise
Founded in Hong Kong by a group of passionate and experienced cybersecurity experts and software engineers.
Innovation
Our comprehensive approach combines cutting-edge technology with human expertise to deliver security solutions.
Trust
We provide businesses with the most reliable and advanced technology solutions to stay ahead in an increasingly complex digital environment.
Results
Our mission is to provide solutions that are not only effective but also practical and sustainable for your business operations.
我們的專家團隊
世界級的網絡安全專業人員,擁有保護您業務的專業知識和認證。
20+ Years Security Experts
Our team consists of certified cybersecurity professionals with expertise across all domains of information security.
10+ Industries Industry Experience
Extensive experience across finance, healthcare, government, and enterprise sectors.
25+ Certs Certifications
Industry-leading certifications and continuous training to stay ahead of emerging threats.
24/7 Support Global Reach
International team providing 24/7 security services and support worldwide.
Professional Certifications
Our team holds industry-leading certifications that validate our expertise and commitment to cybersecurity excellence.

CISSP
Certified Information Systems Security Professional

CISM
Certified Information Security Manager

CISA
Certified Information Systems Auditor

CEH
Certified Ethical Hacker

OSCP
Offensive Security Certified Professional

OSWE
Offensive Security Web Expert

GPEN
GIAC Penetration Tester

GWAPT
GIAC Web Application Penetration Tester

GXPN
GIAC Exploit Researcher and Advanced Penetration Tester

GCTI
GIAC Cyber Threat Intelligence

CRTE
Certified Red Team Expert

CRTP
Certified Red Team Professional

CCSK
Certificate of Cloud Security Knowledge

CIPM
Certified Information Privacy Manager
CDPSE
Certified Data Privacy Solutions Engineer

ISO 27001
Lead Implementer & Auditor

AWS Certified DOP
DevOps Engineer Professional

AWS Certified SAP
Solutions Architect Professional

AWS Certified
Machine Learning Specialty

AWS Certified
Security Specialty
Ready to work with certified security professionals?
Contact Our Experts我們的解決方案
我們提供全面的安全及開發服務,助您建立穩固的數碼業務基石。
滲透測試流程

什麼是滲透測試?
滲透測試是一種模擬網絡攻擊的安全評估方法,旨在評估系統的安全性。我們的專家使用與真實攻擊者相同的技術和工具,但目的是幫助您識別和修復漏洞,而不是造成損害。
主動防禦
在攻擊者發現前識別漏洞
真實評估
模擬真實攻擊場景
我們的滲透測試服務
提供全方位的滲透測試服務,從網頁應用到網絡基礎設施,確保您的系統安全無虞。
網頁應用程式測試
深入測試您的網頁應用程式,識別 OWASP Top 10 漏洞及其他安全風險。
- • SQL 注入測試
- • 特權提升測試
- • 認證繞過測試
- • 業務邏輯漏洞
網絡滲透測試
評估您的網絡基礎設施安全性,包括內部和外部網絡環境。
- • 端口掃描與服務識別
- • 特權提升測試
- • 橫向移動模擬
- • 防火牆繞過測試
移動應用程式測試
全面評估您的 iOS 和 Android 應用程式安全性。
- • 靜態代碼分析
- • 動態運行時測試
- • API 安全評估
- • 數據儲存安全
API 安全測試
專業的 API 安全評估,確保您的後端服務安全可靠。
- • REST/GraphQL API 測試
- • 認證與授權測試
- • 參數污染攻擊
- • 率限制繞過
社交工程測試
評估員工對社交工程攻擊的敏感度和防範意識。
- • 網絡釣魚模擬
- • 電話社交工程
- • 物理入侵測試
- • USB 投放測試
詳細報告
提供詳細的測試報告,包含風險評級和修復建議。
- • 執行摘要
- • 技術詳細報告
- • 風險評級
- • 修復優先級
我們的評估服務
漏洞評估
全面掃描和分析您的 IT 基礎設施,識別安全漏洞並提供修復建議。
- 網絡和系統掃描
- 應用程式安全檢測
- 配置錯誤識別
- 詳細修復指南
合規審計
評估您的組織是否符合相關法規和行業標準,確保合規性。
- GDPR / PDPO 合規
- ISO 27001 評估
- PCI DSS 審計
- 合規差距分析
政策審查
全面檢視和改進您的安全政策與程序,確保最佳實踐。
- 安全政策評估
- 程序有效性檢查
- 員工培訓評估
- 政策更新建議
我們支援的合規標準
ISO 27001
資訊安全管理系統國際標準認證,確保您的資訊資產得到適當保護。
- 風險評估與管理
- 安全政策制定
- 員工培訓計劃
- 持續改進流程
PCI DSS
支付卡行業數據安全標準,保護信用卡交易和持卡人數據。
- 網絡安全評估
- 訪問控制實施
- 定期監控測試
- 資訊安全政策
GDPR/PDPO
歐盟通用數據保護條例和香港個人資料私隱條例合規。
- 數據保護影響評估
- 同意管理機制
- 數據主體權利
- 數據外洩應變

為什麼需要安全培訓?
人員是網絡安全防線中最重要也是最脆弱的環節。通過專業的安全培訓,您的員工將成為抵禦網絡威脅的第一道防線,而不是最大的風險。
我們的培訓計劃
網絡釣魚模擬
真實模擬網絡釣魚攻擊,測試和提升員工的識別能力。
- • 電子郵件釣魚測試
- • 社交媒體釣魚
- • 即時訊息釣魚
- • 結果分析報告
安全意識培訓
互動式安全意識培訓課程,涵蓋最新的威脅和防護措施。
- • 密碼安全管理
- • 社交工程防範
- • 安全瀏覽習慣
- • 移動設備安全
事件應變培訓
模擬安全事件場景,訓練員工的應急反應能力。
- • 事件識別流程
- • 應急響應程序
- • 溝通協調機制
- • 事後總結分析
雲安全服務
專業的雲端安全服務,保護您的雲基礎設施免受威脅,確保數據安全和合規性,助力數字化轉型。
雲安全挑戰
雲端環境帶來靈活性和擴展性的同時,也引入了新的安全挑戰。我們幫助您識別和解決這些挑戰,確保雲端部署的安全性。
配置錯誤
不當的雲服務配置可能導致數據外洩
存取控制
複雜的身份和存取管理需求
共享責任
理解雲服務提供商和客戶的安全責任分工

我們的雲安全服務
雲安全評估
全面評估您的雲環境安全態勢,識別潛在風險和改進機會。
- • 配置安全檢查
- • 網絡安全分析
- • 數據保護評估
- • 合規性檢查
安全架構設計
設計安全的雲架構,從零開始構建或改進現有部署。
- • 零信任架構
- • 多重防禦策略
- • 安全網絡分段
- • 最小權限原則
持續監控
24/7 雲環境監控,及時發現和響應安全威脅。
- • 異常行為檢測
- • 日誌分析
- • 威脅獵捕
- • 自動化響應
託管安全服務
24/7 全天候安全監控和管理服務,讓您專注核心業務,我們負責保護您的數字資產安全。
為什麼選擇託管安全?
現代企業面臨的網絡威脅日益複雜,建立和維護內部安全團隊成本高昂。我們的託管安全服務提供專業的安全專家團隊,讓您以更低的成本獲得企業級安全防護。
24/7 監控
全天候威脅檢測和響應
專家團隊
經驗豐富的安全專家
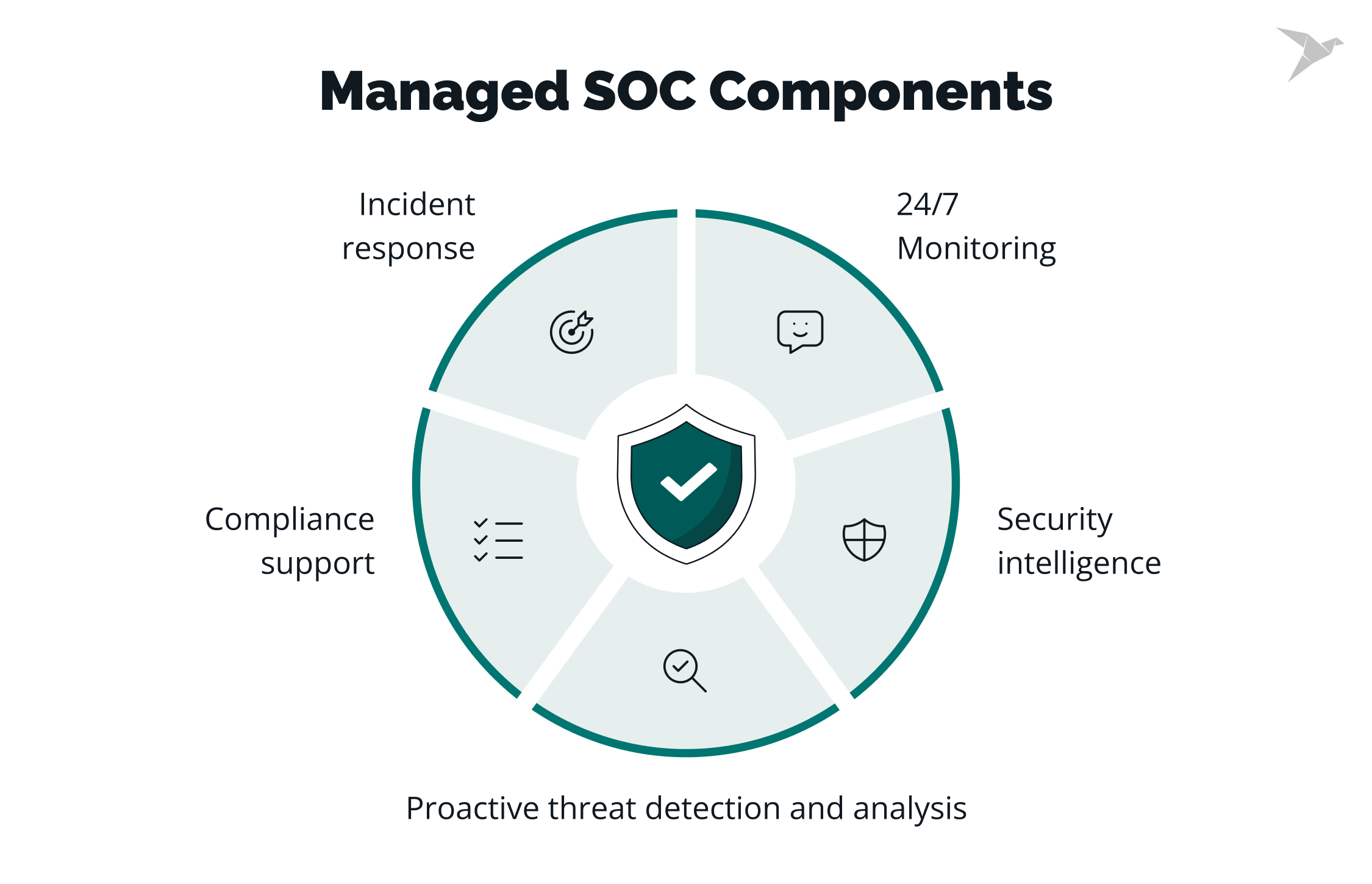
我們的託管安全服務
SOC 服務
專業的安全運營中心,提供24/7監控和事件響應服務。
- • 威脅檢測和分析
- • 事件響應處理
- • 日誌管理分析
- • 安全報告生成
數位取證
專業的數位證據收集和分析,支援事件調查和法律程序。
- • 事件調查分析
- • 證據收集保全
- • 攻擊路徑重建
- • 法律支援服務
威脅狩獵
主動搜尋和識別高級持續性威脅和隱藏的攻擊活動。
- • 高級威脅檢測
- • 威脅情報分析
- • 行為異常檢測
- • 預防性安全措施
我們的安全服務
量身定制的綜合網絡安全解決方案,保護您的業務免受不斷變化的數碼威脅。
滲透測試
全面的安全評估,在攻擊者發現漏洞前識別它們。我們模擬真實世界的攻擊來測試您的防禦。
- 網頁應用程式安全測試
- 網絡安全評估
- 移動應用程式安全測試
- API 安全測試
- SCADA 安全評估
安全風險評估與審計
詳細的安全審計和評估,確保您的系統符合行業標準和監管要求。
- 合規審計
- 風險評估
- 安全策略審查
- 源代碼審查
- 事件應變計劃
合規服務
專家指導,助您達到並維持行業標準,如 ISO 27001 及針對 PDPO、GDPR 和 PIPL 的數據隱私評估。
- ISO 27001 認證
- 隱私影響評估與審計
- PCI DSS 合規
安全培訓
全面的網絡安全培訓計劃,教育您的團隊了解最新的威脅和最佳實踐。
- 網絡釣魚模擬
- 安全意識培訓
- 事件應變培訓
- 安全編碼實踐
雲端安全
通過我們專業的評估和雲安全最佳實踐的實施,保護您的雲基礎設施。
- 雲安全評估與審查
- 雲配置審計
- 容器安全
託管安全服務
24/7 全天候安全監控和事件應變服務,時刻保護您的業務。
- 網絡取證
- 事件應變
- SIEM 管理
- 威脅捕獵
- 安全運營中心 (SOC)
我們的開發方案
定制化的應用程式開發方案,構建穩健且可擴展的數碼產品,將您的願景變為現實。
行動應用程式開發
我們建立直覺、高效能且準備好獲得市場成功的原生和跨平台行動應用程式。
網站設計與開發
我們根據您的業務目標和品牌形象創建美觀、響應迅速且用戶友好的網站。
人工智能解決方案
我們利用人工智能的力量,助您發掘新機會、簡化運作並提供更智慧的體驗。
雲端設計與開發
我們透過實現靈活的基礎設施、即時數據存取和成本效益,雲端解決方案使組織能夠快速適應不斷變化的需求。

我們的開發理念
我們相信技術應該服務於業務目標。我們的開發團隊不僅是編程專家,更是業務解決方案的架構師。我們採用敏捷開發方法,確保每個項目都能快速響應市場變化,同時保持代碼質量和系統穩定性。
敏捷開發
快速迭代,及時交付
質量保證
嚴格的測試與代碼審查
我們的開發服務
提供全方位的軟件開發服務,從移動應用到企業級系統,確保您的數字產品高效可靠。
移動應用程式開發
為 iOS 和 Android 平台開發原生和跨平台移動應用,提供卓越的用戶體驗。
- 原生 iOS/Android 開發
- React Native/Flutter 跨平台
- UI/UX 設計優化
- 應用商店發布支援
網頁應用程式開發
使用現代前端和後端技術棧,開發響應式、高性能的網頁應用程式。
- React/Vue/Angular 前端
- Node.js/Python 後端
- 響應式設計
- 性能優化
人工智能解決方案
利用機器學習和深度學習技術,開發智能應用程式,提升業務效率和用戶體驗。
- 機器學習模型開發
- 自然語言處理
- 計算機視覺應用
- 預測分析系統
雲端架構與開發
設計和實現可擴展的雲原生應用程式,利用雲服務的優勢實現高效能和成本效益。
- AWS/Azure/GCP 架構
- 微服務架構設計
- 容器化與編排
- 無伺服器應用開發
DevOps 與持續交付
建立自動化的開發、測試和部署流程,實現快速、可靠的軟件交付。
- CI/CD 流水線搭建
- 基礎設施即代碼
- 監控與日誌管理
- 自動化測試與部署
維護與支援服務
提供持續的技術支援、性能優化和功能更新,確保您的應用程式始終保持最佳狀態。
- 24/7 技術支援
- 定期安全更新
- 性能監控與優化
- 功能擴展與升級
為何選擇 Byte-Tron
我們的專業團隊與卓越技術,是您最值得信賴的合作夥伴。
豐富行業經驗
團隊成員在金融、電信和政府機構等領域擁有多年實戰經驗,深刻理解各行業的獨特挑戰。
頂尖技術認證
我們的專家持有OSCP、CISSP等多項國際頂級安全認證,確保服務質量達到最高標準。
客戶至上
我們致力於與客戶建立長期合作關係,提供量身定制的解決方案,並確保項目成功交付。
關於我們
Byte-Tron Solutions 成立於香港,由一群充滿熱情且經驗豐富的網絡安全專家和軟件工程師組成。我們的使命是為企業提供最可靠、最先進的技術解決方案,幫助客戶在日益複雜的數碼環境中保持領先地位。我們相信,技術不僅是工具,更是推動業務創新和增長的關鍵力量。
專業團隊
世界級的網絡安全專家,擁有保護您業務所需的專業知識和認證。
20+ 年資安專家
我們的團隊由認證網絡安全專家組成,在資訊安全各領域擁有專業知識。
10+ 行業經驗
在金融、醫療、政府和企業等領域擁有豐富經驗。
25+ 專業認證
業界領先的認證和持續培訓,確保領先新興威脅。
24/7 全球支援
國際團隊提供全球 24/7 安全服務和支援。
專業認證
我們的團隊持有業界領先的認證,驗證我們在網絡安全領域的專業知識和卓越承諾。

CISSP
Certified Information Systems Security Professional

CISM
Certified Information Security Manager

CISA
Certified Information Systems Auditor

CEH
Certified Ethical Hacker

OSCP
Offensive Security Certified Professional

OSWE
Offensive Security Web Expert

GPEN
GIAC Penetration Tester

GWAPT
GIAC Web Application Penetration Tester

GXPN
GIAC Exploit Researcher and Advanced Penetration Tester

GCTI
GIAC Cyber Threat Intelligence

CRTE
Certified Red Team Expert

CRTP
Certified Red Team Professional

CCSK
Certificate of Cloud Security Knowledge

CIPM
Certified Information Privacy Manager
CDPSE
Certified Data Privacy Solutions Engineer

ISO 27001
Lead Implementer & Auditor

AWS Certified DOP
DevOps Engineer Professional

AWS Certified SAP
Solutions Architect Professional

AWS Certified
Machine Learning Specialty

AWS Certified
Security Specialty
Get in Touch
Ready to secure your business? Contact our cybersecurity experts for a free consultation.
Contact Information
Call Us
+852 3575 0895
24/7 Emergency Support
Visit Us
Unit C, Floor 4, China Insurance Building
No. 48 Cameron Road, Tsim Sha Tsui, Kowloon, Hong Kong
Emergency Response
Experiencing a security incident? Our rapid response team is available 24/7 to help contain and resolve critical security threats.
Emergency Contact